2024 铁人三项 决赛 Misc - BlindFlowanalyis
流量包初步分析
总共给了两个文件
- webflow1.pcap
- webflow2.pcap
先对 webflow1.pcap 进行分析
前面部分都是目录爆破的流量,到了后面部分
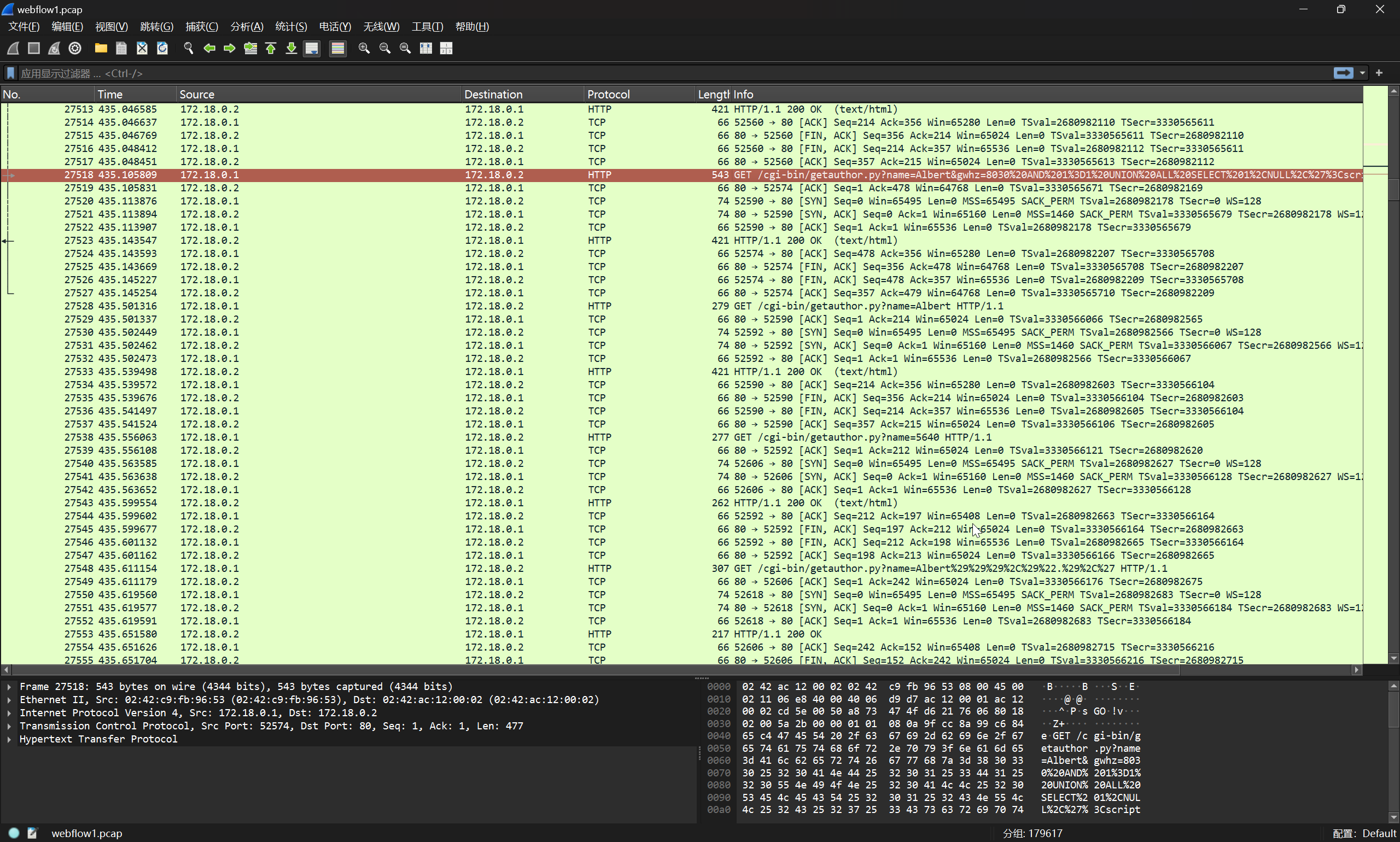
很明显的就是 sql 注入的语句,将 sql 注入的语句进行提取
tshark -r webflow1.pcap -T fields -Y 'http.request.uri.path =="/cgi-bin/getauthor.py"'-e http.request.uri | perl -MURI::Escape -lne'print uri_unescape($_);' > webflow1.pcap.sql
然后编写脚本从其中筛选出来含有的表
with open("webflow1.pcap.sql", "r") as f:
data_sql = f.read().strip().split("\n")
data_sql = [i.split(" ") for i in data_sql]
data_sql = [[j.lower() for j in i if j != ""] for i in data_sql]
res = []
for i in data_sql:
if "from" in i:
index_FROM = i.index("from")
data_table = i[index_FROM + 1].split(")")[0]
if data_table in res:
continue
else:
res.append(data_table)
print(res)
print("\n-".join(res))
在其中得知存在有一下表
- msysaccessobjects
- sysibm.sysdummy1
- rdb$database
- information_schema.io_statistics
- information_schema.system_users
- sysmaster:sysdual
- versions
- system.onerow
- dual
- sqlite_master
- secret
- flagdata
同理,对 webflow2.pcap 进行同样的操作
- flagdata
提取敏感信息
那么就很明显了,有两个表 secret 和 flagdata 需要注意
找到两个表的所有相关流量
信息
盲注的相关记录太多了,所以做了隐藏
webflow1.pcap
$ tshark -r webflow1.pcap -T fields -Y 'http.request.uri.path =="/cgi-bin/getauthor.py"'-e http.request.uri | perl -MURI::Escape -lne'print uri_unescape($_);' | grep secret
/cgi-bin/getauthor.py?name=Albert'union/**/select name,pub_key,private_key,contract,datetime,1,1,1,1 from secret where'1'='1
tshark: The file "webflow1.pcap" appears to have been cut short in the middle of a packet.
/cgi-bin/getauthor.py?name=Albert'union/**/select name,pub_key,private_key,contract,datetime,1,1,1,1 from secret where'1'='1
webflow2.pcap
$ tshark -r webflow2.pcap -T fields -Y 'http.request.uri.path =="/cgi-bin/getauthor.py"'-e http.request.uri | perl -MURI::Escape -lne'print uri_unescape($_);'| grep"flagdata"| grep -e"union"
/cgi-bin/getauthor.py?name=Albert'union/**/select name,flagdata,note,datetime,1,1,1,1,1 from flagdata where'1'='1
很好,是直接联合查询而不是盲注,那么去找到对应流量提取返回包
(http.request.uri.path == "/cgi-bin/getauthor.py") && (http.request.uri.query.parameter contains "secret")
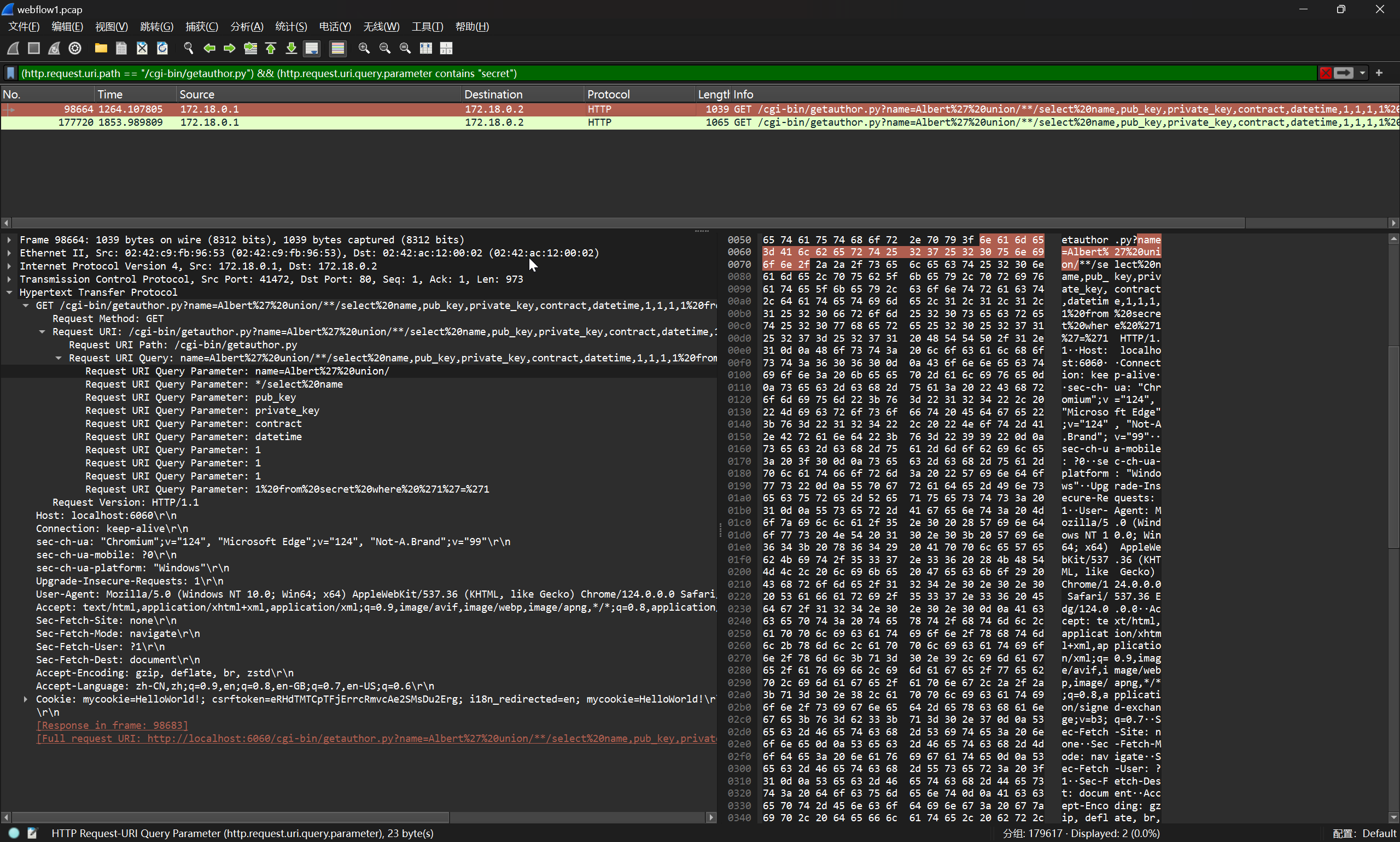
查看返回包
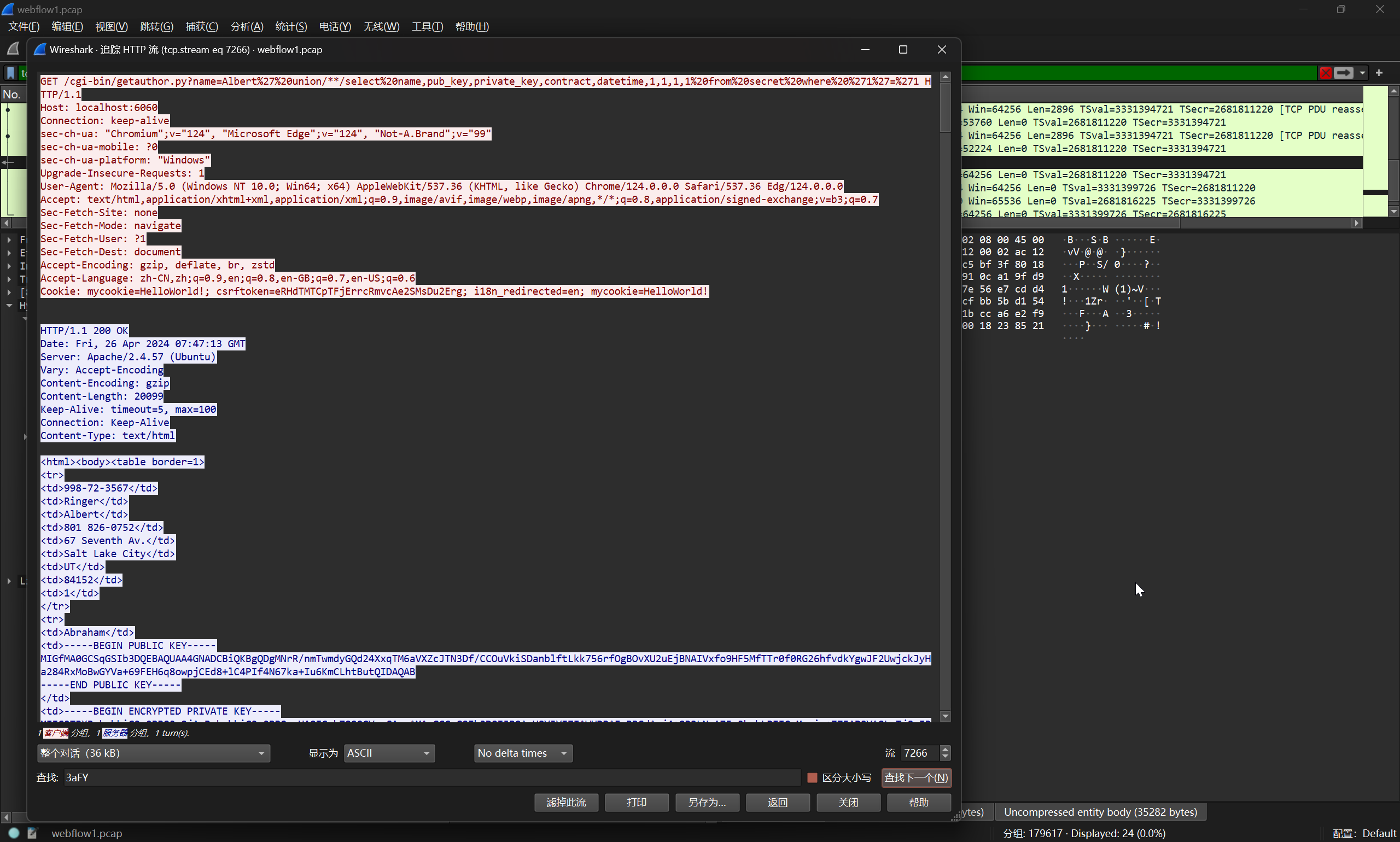
在其中关注到 admin 账户的密钥
-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQDBtGmqBdtXPN9TcBo9UXwHbozxSjAgOk4sfOTYhbWgjcp8ia2BaIsHUfOB2SpevVejexwNxDFOo6v/mycoFOF8wqpiii8tGTVB+FBo39YKkBI4yI863VsB3NJV8gedFZAybEUkwkFhGN7mVs9XTaYYrHXNFWRIxjvnjQtpMnAvvQIDAQAB
-----END PUBLIC KEY-----
-----BEGIN ENCRYPTED PRIVATE KEY-----
MTTC3TBXBgkqhkiG9w0BBQ0wSjApBgkqhkiG9w0BBQwwHAQIVLQmLXnlUYkCAggAMAwGCCqGSIb3DQIJBQAwHQYJYIZIAWUDBAEqBBBCQKgOObf2BrhJ9tHvAb4oBIICgP3WaNdtO3oTAX1GjdqBL0f6HvFZ9q25EIOAah78rfhKNrJQP0uHHUnbIDKUZTSMwNZ7kNQAAnJPdjwhZVNbymCjUrVvqs0VD8GWncUlIIxrAkpsgqioABSKLoy280ubg2s1IV/sqbuuvN4ldPvnAvyrLLnNLgGyU86v2Q1ArFWfG4kgeZSpW06W6TwgeIZbjRSnLKFXx1VEhpZSCOadg/HOh8BfLbFlZiWgDiuTdVSzGq34fLV8jKYfUjhEffh/tCNhjU5E8M6ItqgXZYyjbBO2ujewBzV1JiBE0QvcavwT8JvV2IDQXBtQmBJZXH4Vqoo2n5YmUgUFDxoZSdAqOfh5kcgO0OgORhOrX/qNisaDfBMwGx2csywJBuSujzZ3ckV3Gv2ysMzRPKfyZ/v10zElsrKZHci2wDMZ4XYqNyvPDafWaxkSNXP64eYRS8J6WVgWycaPq0LkoJnuxtmOnlYlZ8cmY2zOf4WfyG7X+NhK6CllS0or2Y7fuqo80dmGTrg7cuVA1GguRMA6qZAOlbqu8zT53vGUOIHDRQFb8DUU5H6t+I3e0+0Qj8ZwgTtUMCx2/WLc0YAq18Al9okrtsxuYIQ815SSxXKOXZsX93hACLEFFkKOW7vNdBMJdVJnbPoaMotkDYtH/d8TYPrrtyOhPRa/Xl8BzA9J40Z3PE+5XaQfTC4Wx9GMb3y/Dv1lVXrAd9XvCPD8jr6tu+aQWpMAq0uLpF0kgyS/5FDfIpiEHMMuRQ+FBKS58HWVkX1yKNmXkljJRpwe53AHLuDgt+0LNhry+5ck2GFH7bkxU13WmotrtUtnSdIX7FZrQzbJmbwHiyMi7oGdKT7vxkr3aFY=
-----END ENCRYPTED PRIVATE KEY-----
同样的,找到 flagdata 表中,用户 admin 的数据
MDgnetOpihRoTmbreC2P7EQqkmeHloAWQ0SA2gKuHWPUP3u8u81ewsTnlyhvc7qL
MMpVl36M9Z0Hu++yIKt2C/mimOFH04ixQAUo5y8h8vajw7vRLwfhpxC+pSjWvxjP
2ieWVgdmXraijq92K6vdXod/SVaOyBT/1/asqhq1abQ=
解密信息
注意
需要注意的是,在 BEGIN ENCRYPTED PRIVATE KEY 头部的 MTTC 需要更改为 MIIC 才能正确识别,因为 PKCS #8 format
尝试��使用 第一届 “长城杯” 信息安全铁人三项赛线下决赛 - WriteUp 中提供的密码爆破脚本
from Crypto.PublicKey import RSA
from rich.progress import Progress
# 读取加密的私钥文件
file_in = open("private.pem", "rb")
encrypted_key = file_in.read()
file_in.close()
# 密码爆破函数
def passphrase_cracker():
# 读取密码字典文件
with open("/usr/share/wordlists/rockyou.txt", "r", encoding="latin-1") as file:
passwords = file.readlines()
print(1)
# 尝试每个密码
with Progress() as progress:
task = progress.add_task("Processing...", total=len(passwords))
for password in passwords:
passphrase = password.strip()
progress.update(task, advance=1)
try:
key = RSA.import_key(encrypted_key, passphrase=passphrase)
print(f"Passphrase cracked: {passphrase}")
print("n = %d" % key.n)
print("e = %d" % key.e)
print("d = %d" % key.d)
print("p = %d" % key.p)
print("q = %d" % key.q)
break # 如果找到正确的密码,停止循环
except ValueError:
continue
# 调用密码爆破函数
passphrase_cracker()
以及 Hashcat 工具,配合 rockyou 字典进行爆破,均失败了
这里直接附上解密后结果
from Crypto.PublicKey import RSA
import libnum
import gmpy2
n = 136024092362152689710172713899392826085562613819502637163574709012959800908069097569347489959246188000879909455954675900898187256462694001680199507890264369748020986792003039927832146357618380320485640247974651461597017754521523478582789651823653650205470697891883134131193787384293246455773119816555908050877
e = 65537
d = 96983349311172448114610684077344531859866705158061854017461211652174689366790434748659538326833645524163686606777761277160529104669611099325734812475218305914063705028257975357368955813173682894994622796568980398528404622799756620123598161913849740935593865664141149764560174893499019267153779766584891066853
p = 12048894621399454101058574170146672880023504304935502855438830209547540828334463319100866266089541071671086068945870668091434002554455832672446379382564831
q = 11289342021513486663717934560260253958877903230700176094000844663541917077757746704211638621740652499799934180688739478331856827700031454191788549757111267
c = "MDgnetOpihRoTmbreC2P7EQqkmeHloAWQ0SA2gKuHWPUP3u8u81ewsTnlyhvc7qLMMpVl36M9Z0Hu++yIKt2C/mimOFH04ixQAUo5y8h8vajw7vRLwfhpxC+pSjWvxjP2ieWVgdmXraijq92K6vdXod/SVaOyBT/1/asqhq1abQ="
import base64
c = base64.b64decode(c.encode())
c = libnum.s2n(c)
phi = (p - 1) * (q - 1)
d = gmpy2.invert(e, phi)
m = pow(c, d, n)
print(libnum.n2s(int(m)))
# flag{182w3t-he5dr4y8g-gy590-gggtd46nd-dgw3456utg676}